In a seminal judgement delivered on August 24, 2017, India’s Supreme Court unanimously ruled that the “right to privacy is protected as an intrinsic part of the right to life and personal liberty…and as a part of the freedoms guaranteed by the Constitution.” This historic judgement is the outcome of petitions challenging the collection of biometric data by the government for its Aadhaar database and WhatsApp’s announcement to share data with Facebook—two cases where the notion of privacy is being put to test in the digital age. Since both biometrics and social media are now practically ubiquitous, this judgement has wide ramifications for the global discourse on how both state and non-state actors collect, protect and use this information.
While the right to privacy decision has not specifically pronounced a judgement on the constitutionality of Aadhaar (it will be decided by a separate bench of the Supreme Court), the judgement stated that “(t)echnological change has given rise to concerns which were not present seven decades ago and the rapid growth of technology may render obsolescent many notions of the present." However, the Supreme Court advised the government to create a "robust regime of data protection ensuring a careful and sensitive balance between individual interests and legitimate concerns of the State…(including) preventing the dissipation of social welfare benefits.”
Aadhaar has already demonstrated the potential of digital ID to transform systems of governance and increase efficiency of private transactions. By addressing the genuine concerns of individual privacy and data protection, it will be ready to move ahead and lead by example as it has already done on the technological side. The right to privacy judgement is an opportunity to make the world’s largest experiment in digital governance a bigger success than it already is. In this blog post I will explain how India can learn from other countries to do just that.
Changing how Indians interact with the state
Preventing leakage of government expenditure and ensuring inclusive growth is the original justification for Aadhaar which is now the largest biometric database in the world with over 90 percent of 1.25 billion Indians enrolled in the program. Until now, Aadhaar has had a relatively smooth ride, much like cruising on a relatively empty highway. Following a remarkably rapid rollout, Aadhaar has been widely accepted as a proof of identity, used as an instrument to expand banking and mobile phone services and restructure the delivery of basic services and subsidies, including the widely acclaimed cooking gas subsidy reform. Aadhaar’s authentication capabilities are driving digital applications in public food distribution systems (PDS), social pensions, mobile payments etc., impacting the lives of millions of people and billions of dollars in public resources. Aadhaar is changing the way ordinary people interact with the state but is also asking them to trust it to keep private information safe in an increasingly interconnected world.
Three attributes of ID systems
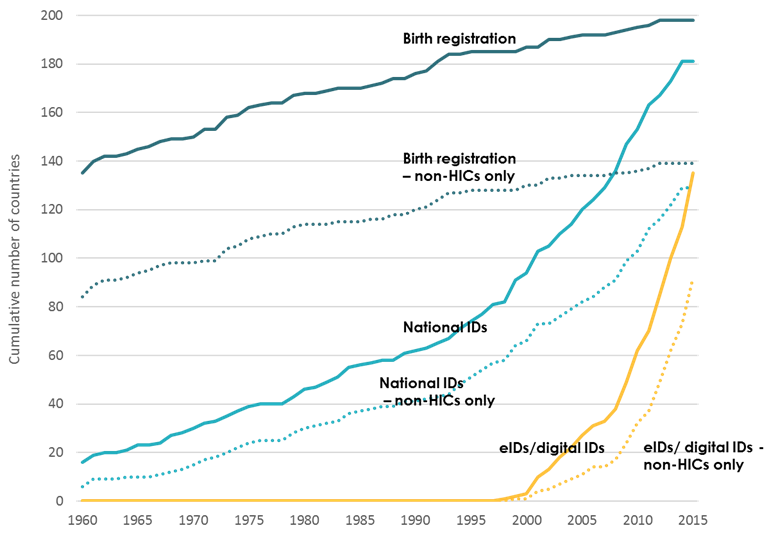
Resolving the issue of individual privacy and data security is therefore of utmost importance. India is not alone in facing this challenge. From the beginning of this century, there has been a rapid spread in identification programs both in high income countries (HICs) as well as in the developing world (see chart).
Identification Programs in High-Income (HIC) and Other Countries
From the earliest times, identification systems have relied on some subset of the many different attributes that together distinguish each of us as a distinct person. They may be bundled into three main factors and combined in different ways to form the basis for identification:
- Something you are: a biometric—physical appearance, or a distinctive voice or smell or behavioral pattern. This is surely the oldest form of recognition, as well as the most recent. In modern digital times, it can encompass digital biometrics such as fingerprint, iris or finger-vein-patterns, voice patterns, DNA, dynamic signature or, on a computer, keystroke rhythms or mouse movement patterns.
- Something you have: a birth certificate, an ID card or a mobile ID, token or other physical credential. Something you have could also be a person—a well-respected and credible individual ready to vouch for you. The best identifier for an infant is still probably its mother.
- Something you know: a personal identification number (PIN) or password, or the ability to provide personal information that is unlikely to be known by others.
There are examples of modern identification systems that combine all three identification factors: have, know and are. Estonia’s pioneering digital ID system is the best example. At the age of 15 fingerprints are taken on registration for the digital ID (who you are: to prevent multiple identities). A card is issued (what you have); it includes digital certificates to enable the holder to both authenticate his identity and to sign documents electronically. For these purposes, the holder authenticates himself against the card by providing two user-selected and private PINs (what you know), one to authenticate himself and the other to sign. Multi-factor authentication offers extra security relative to the use of only one factor. The main difference with Aadhaar is the option of the private PINs which gives the individual control over the authentication process and reduces the chance of impersonation without his or her knowledge, ensuring greater degree of privacy over the centrally warehoused information.
Control over data sharing
Countries have taken several approaches to mitigating the risks associated with integrated identification systems—something Aadhaar’s critics have repeatedly pointed out. One approach is to provide for multiple identifiers while still ensuring that identity itself is unique. This corresponds to the idea that a single, unique individual should be able to be identified in different ways for different purposes. In Austria’s distinctive system, cryptography enables users to access multiple government services using a single e-ID while ensuring that records cannot be matched across the different databases using a common number. Each e-ID card includes a unique personal identifier, the Source PIN, which is stored only on the card and cannot be held by any government body or private entity. When a card-holder wants to access a service using the card, a unique sector-specific identifier, called the sector-specific PIN or SS-PIN, is generated from the Source PIN using a one-way cryptographic function. The SS-PIN is different for each service and also for different private sector applications. It is not possible to derive one SS-PIN from another, for example, to generate the tax SS-PIN from the social security SS-PIN. Neither can an SS-PIN be used to calculate the Source PIN.
This unique system enables card holders to use the same credential to authenticate themselves for all purposes, but prevents the consolidation of their records using a common number although, of course, it does not prevent the use of names or other biographic data to compare records. The generation of SS-PINs without the card is only possible for the source-PIN Register Authority and is only permissible when personal data are to be processed or transmitted in conformity with the Data Protection Act of 2000.
These are just two examples of several possible country experiences that India can learn from. The Supreme Court judgement should serve as a pause button to take stock of what has been achieved and how it can go further while protecting ‘informational privacy’ as the Court has ruled.
Disclaimer
CGD blog posts reflect the views of the authors, drawing on prior research and experience in their areas of expertise. CGD is a nonpartisan, independent organization and does not take institutional positions.





